Citadel Programming Lab

Secure Coding Game-Based Lab
The Citadel Programming Lab is an online virtual secure coding game-based computer lab. The Lab combines a tower defence game with 6 security programming tasks.
The lab is based on a serious game approach to join learning and playfulness. The lab’s platform combines a Unity game linked with a coding environment based on an instance of GitLab. The game elements and coding exercises are linked to CyBOK, the Cybersecurity Body of Knowledge, to map its cybersecurity content.
Tower Defence Game and Coding Tasks
The game elements and game loops are designed to illustrate cybersecurity processes. The player uses mouse and keyboard to activate the different towers forming the defence against vehicles potentially harmful. The towers can be improved by gaining points while playing the game level or by taking security programming tasks. The tasks are aligned to the security role of the tower.
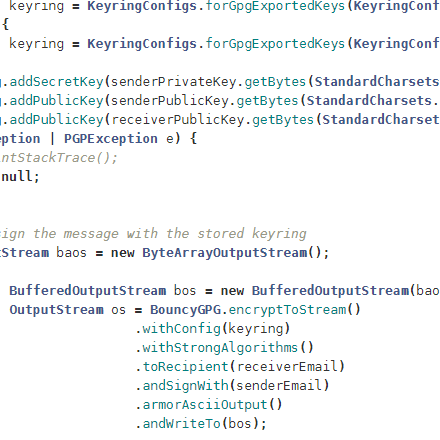


CyBOK Linkage
The cybersecurity content of the lab and its learning outcomes are linked to the Knowledge Areas and Topics of CyBOK v1.1. In the lab, both the programming tasks and the game elements and metaphors cover aspects of topics of the following CyBOK v1.1 Knowledge Areas: Adversarial Behaviours, Applied Cryptography, Authentication, Authorisation & Accountability, Distributed System Security, Law & Regulation, Network Security, Privacy & Online Rights, Risk Management & Governance, Secure Software Lifecycle, Security Operations & Incident Management, Software Security, Web & Mobile Security.
Tasks
The following table shows the list of CyBOK Topics linked to the lab’s programming exercises.
Note that three of the tasks originate from the paper and research by Y. Acar, C. Stransky, D. Wermke, M. L. Mazurek and S. Fahl titled Security Developer Studies with GitHub Users: Exploring a Convenience Sample presented at the Symposium on Usable Privacy and Security SOUPS 2017.
| Coding Tasks | CyBOK Knowledge Areas | CyBOK Topics | |
|---|---|---|---|
| All exercises | Software Security | coding practices | |
| Secure Software Lifecycle | motivations for secure software lifecycle | ||
| Risk Management & Governance | risk assessment | ||
| Applied Cryptography | Cryptographic Libraries | ||
| PGP | Applied Cryptography | Managing Public Keys and Public Key Infrastructure | |
| Applied Cryptography | Digital Signatures | ||
| Web & Mobile Security | web PKI and HTTPS | ||
| Network Security | Public Key Infrastructure | ||
| Law & Regulation | electronic signatures and indentity trust services | ||
| Certificates | Applied Cryptography | Managing Public Keys and Public Key Infrastructure | |
| Applied Cryptography | Binding Public Keys and Identities via Certificates | ||
| Web & Mobile Security | web PKI and HTTPS | ||
| Network Security | Public Key Infrastructure | ||
| SSL | Network Security | TLS (Transport Layer Security) | |
| Applied Cryptography | Difie-Hellman Key Exchange | ||
| URL shortener | Privacy & Online Rights | obfuscation-based inference control | |
| Privacy & Online Rights | privacy engineering | ||
| Risk Management & Governance | risk assessment | ||
| Credentials | Software Security | SQL injection | |
| Software Security | query generation | ||
| Applied Cryptography | Hash functions | ||
| Law & Regulation | prescriptive jurisdiction and data protection | ||
| Web & Mobile Security | input sanitisation | ||
| Web & Mobile Security | SQL-injection | ||
| Web & Mobile Security | password leaks | ||
| String encryption | Privacy & Online Rights | privacy engineering | |
| Privacy & Online Rights | cryptography-based access control | ||
| Applied Cryptography | Authenticated Encryption(AE)schemes | ||
| Applied Cryptography | Cryptographic Libraries |
Game
The following table shows the list of CyBOK Topics linked to the lab’s game elements and associated game metaphors.
| Game Elements | CyBOK Knowledge Areas | CyBOK Topics |
|---|---|---|
| Simple Vehicle | Software Security | coding practices |
| Risk Management & Governance | risk assessment | |
| Tank | Privacy & Online Rights | obfuscation-based inference control |
| Privacy & Online Rights | privacy engineering | |
| Hacker | Adversarial Behaviours | Hacktivists |
| Web & Mobile Security | password leaks | |
| Web & Mobile Security | SQL-injection | |
| Interceptor | Applied Cryptography | Managing Public Keys and Public Key Infrastructure |
| Applied Cryptography | Binding Public Keys and Identities via Certificates | |
| Network Security | TLS (Transport Layer Security) | |
| Web & Mobile Security | web PKI and HTTPS | |
| Network Security | Public Key Infrastructure | |
| Standard Turret | Software Security | coding practices |
| Risk Management & Governance | risk assessment | |
| Web & Mobile Security | input sanitisation | |
| Applied Cryptography | Hash functions | |
| Communication Tower | Network Security | Networking Infrastructure Security |
| Network Security | Cloud and Data Center Security | |
| Distributed System Security | reliable and secure group communication | |
| Missile Turret | Network Security | device fingerprints |
| Adversarial Behaviours | Attribution | |
| Security Operations & Incident Management | cyber-threat intelligence (CTI) | |
| Laser Turret | Network Security | TLS (Transport Layer Security) |
| Web & Mobile Security | web PKI and HTTPS | |
| Watch Tower | Applied Cryptography | public-key schemes with special properties |
| Applied Cryptography | Binding Public Keys and Identities via Certificates | |
| Authentication, Authorisation & Accountability | accountability | |
| Radar | Authentication, Authorisation & Accountability | authentication |
| Applied Cryptography | public-key schemes with special properties | |
| Applied Cryptography | Binding Public Keys and Identities via Certificates |
Trying or Using the Lab
If you are interested in trying, using, deploying the Citadel Programming Lab, please let us know using this online form (repeated below).
The Citadel Programming Lab sources are available under GNU AGPLv3 Licence at: https://gitlab.com/citadel-programming-lab/citadel-programming-lab
Research Funding and Support
The Citadel Programming Lab is developed as part of a joint interdisciplinary research between Heriot-Watt University and the Glasgow School of Art.
The research was supported by:
- NCSC-RISCS Developer-Centred Security approach in 2017-18, PI Manuel Maarek, Co-I Sandy Louchart.
- EPSRC Secrious Project Expansion into an education virtual computer lab in 2021.
- CyBOK Development of the link with CyBOK v1.1, packaging and dissemination in 2021-22, PI Manuel Maarek, Co-I Sheung Chi Chan.
Project Members
- Manuel Maarek (Heriot-Watt University)
- Sandy Louchart (Glasgow School of Art)
- Léon McGregor (Heriot-Watt University)
- Ross McMennemy (Glasgow School of Art)
- Sheung Chi Chan (Heriot-Watt University)
- Callum Jones (Heriot-Watt University)
- Szymon Wlodarczyk (Heriot-Watt University)
Publications
- [EuroUSEC-2019]
-
Manuel Maarek, Léon McGregor, Sandy Louchart, and Ross McMenemy.
How Could Serious Games Support Secure Programming? Designing
a Study Replication and Intervention.
EuroUSEC European Workshop on Usable Security 2019.
[ DOI ] - [GaLA-2018]
-
Manuel Maarek, Sandy Louchart, Léon McGregor, and Ross McMenemy.
Co-created Design of a Serious Game Investigation into
Developer-Centred Security.
GaLA Games and Learning Alliance 2019.
[ DOI ]




